Tech Talk | Medical Device Cybersecurity: What You Need to Know
Like IoT devices, medical devices may be made up of various components: the physical device, the network interface, the mobile app used to control the device and exchange data, and a cloud service used to collect and share the data.
 Mike Robey, MS, AAO-HNS/F Senior Director, Information Technology
Mike Robey, MS, AAO-HNS/F Senior Director, Information Technology
Ever since the first iPhone was released in June 2007, things have become more connected. Today, there is an app for everything. Medical devices are no exception. They have become an important subset of the Internet of Things (IoT) discussed in the May 2022 edition of the Bulletin.1 This article expands on the earlier IoT piece to discuss what you need to know to keep medical devices cybersecure.
Medical devices are a broad category, not all are apps. Cybersecurity is one aspect. It would be impossible to cover everything within a single article. Still, medical device cybersecurity, along with data protection and privacy, is an emerging and important topic. The intent here is to provide background material and preliminary guidance for further investigation.
Everything Is Connected
Like IoT devices, medical devices may be made up of various components: the physical device, the network interface, the mobile app used to control the device and exchange data, and a cloud service used to collect and share the data. Each of these components can represent different attack vectors.
To be properly protected, security must be designed in at every layer including hardware and software. A complete understanding requires knowing how each of the components are constructed and how these interact with one another. This is difficult and time consuming to do. Many decisions are based on the reputation of the manufacturer and, in the United States, the medical device’s approval from the Food and Drug Administration (FDA).
From an overview perspective, keep in mind aspects of the Health Insurance Portability and Accountability Act (HIPAA), Zero Trust cybersecurity framework, and Universal Design as they apply to medical devices.
With respect to the data associated with a medical device, the three principles of HIPAA still apply:
- Confidentiality: Data are not made available nor disclosed to unauthorized people
- Integrity: Data, while at rest or in transit, are not altered, changed, or destroyed in an unauthorized manner
- Availability: Data are access assessable and usable on demand by authorized people
Zero Trust is the National Institution of Standards and Technology (NIST) modernized cybersecurity framework. Perimeter-based security is no longer enough. With cloud-based computing, it is harder to even define the perimeter. Zero Trust brings to light four principles:2
- There are multiple points of attack
- An attack at one point puts all at risk
- User privileges should be minimized
- The assumption that the network has already been compromised must prevail; every device needs to be continuously protected and authenticated
Zero Trust applies more to medical devices used in a hospital or clinical setting. Nevertheless, Zero Trust is important background to know, especially when medical devices are connected to a network.
Depending on their purpose, medical devices' usage and effectiveness are related to how the seven Universal Design Principles are applied:3
- Equitable use: Design for all
- Flexibility in use: Design for each—is the device ADA compliant?
- Simple and intuitive: Design for the mind
- Perceptible information: Design for the senses
- Tolerance for error: Design for error—make sure the device requests confirmation before taking irreversible or potentially critical operations
- Low physical effort: Design for limited strength or stamina
- Size and space for approach and use: Design provides usability for all regardless of body size, posture, or mobility
Not all Universal Design Principles will apply in every case. Keep the principles of HIPAA, Zero Trust, and Universal Design in mind as you review the manufacturer’s literature describing a medical device and its purpose.
Software Bill of Materials (SBoM)
From a cybersecurity perspective, it is crucial to understand the software components included in a medical device. Open-source software is prevalent in the development of smartphone apps and cloud-based software. This is not a bad thing since most widely used open-source software have large programmer communities that keep the code bug-free and feature rich. However, new software vulnerabilities are reported every day.4 Without knowing the software components embedded in a medical device and regular checks for the latest vulnerabilities, you cannot know if its usage is at risk.
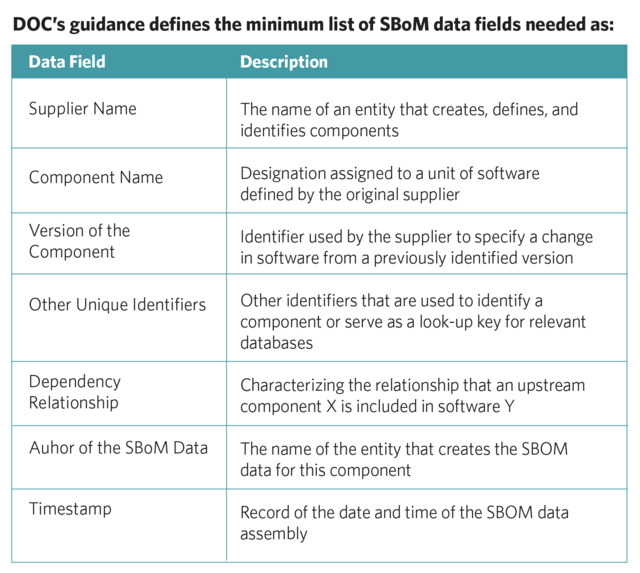
The audience for most of the recent medical device cybersecurity literature are the manufacturers. Latest developments in the public sector have placed emphasis on SBoM. Executive Order 14028 on Improving the Nation’s Cybersecurity led to the U.S. Department of Commerce (DOC) releasing guidance on the minimum elements for a SBoM.5 The FDA’s recent draft guidance on medical device cybersecurity6 includes a large concentration on SBoM.
To be more effective, SBoM information needs to be received electronically7 so that software components can be more easily associated with updated vulnerabilities. This is an essential part of Vulnerability Management—the ongoing, regular process for identifying, assessing, and remediating cyber vulnerabilities across medical devices in use.
 What You Need to Know
What You Need to Know
For physicians, in addition to the SBoM, look for the manufacturer’s label and regularly check the manufacturer’s post market reporting.8 If the medical device transmits data, make sure it uses strong encryption. Make sure you have the manufacturer’s contact information and understand the expected level of support the manufacturer can provide. Keep an inventory of the medical devices used by patients.
Patients need to know what to do to maintain the device’s cybersecurity over its lifetime. Users need know how to keep the device patched as well as understand the device’s potential risks and other relevant information. These things need to be kept in mind as the patient reviews the device’s literature. Equally important, does the patient know who to contact if the device malfunctions? Do they understand what data are collected and to whom the data are transmitted?
This article covered a lot of ground. Several subject areas such as Zero Trust and Universal Design may be tangential to medical device cybersecurity, but in today’s world, everything is connected. With attack vectors at every component, security is essential at all layers. Vulnerability Management is crucial to staying on top of daily susceptibilities and exploitations. Users need to be informed on how to mitigate new risks in a timely manner. At the end of the day, you must weigh the benefits of a medical device against how important it is for the patient to read and understand a 200+ page users guide.
References
- https://bulletin.entnet.org/home/article/22197353/techtalk-internet-of-things-iot-cybersecurity-what-you-need-to-know
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
- https://www.washington.edu/doit/universal-design-process-principles-and-applications
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- https://www.ntia.doc.gov/files/ntia/publications/sbom_minimum_elements_report.pdf
- https://www.fda.gov/regulatory-information/search-fda-guidance-documents/cybersecurity-medical-devices-quality-system-considerations-and-content-premarket-submissions
- How to receive SBoM electronically would require an in-depth article and the ability to do so may be out of scope for most small practices.
- https://www.fda.gov/medical-devices/medical-device-safety/medical-device-reporting-mdr-how-report-medical-device-problems